昨天,有网友反映Github网站无法访问,怀疑是攻击者发起了大规模的中间人劫持。除了 Github 网站,京东、koajs 等其他网站似乎也受到了影响。
攻击似乎是通过骨干网劫持443端口。经测试,DNS系统解析完全正常。目前主要是部分地区用户受到影响,移动、联通、电信、教育网等运营商均能重现劫持问题,国外网络访问这些网站均未出现异常。
由于攻击者使用的自签名证书不受所有操作系统和浏览器的信任,因此用户在访问这些站点时可能会遇到安全警告。
截至3月27日12点已阻止此网站显示有安全证书错误的内容,根据Bluepoint.com部分信息的动态更新,网友反映Github网站无法访问,攻击规模似乎进一步扩大。
从网上查询到的信息可以看出,GitHub.io是此次攻击涉及范围最广的。查看证书信息可以发现,这些网站的证书被攻击者使用的自签名证书替换,导致浏览器不可信,无法访问。
图片来自v2ex网友
在自签名证书邮箱被替换之前,显示证书的创建者被昵称为心是山灵(QQ346608453),这个心是山灵似乎是这次攻击的始作俑者。幸运的是,绝大多数当前网络所有网站都开启了加密技术来抵御劫持,所以用户访问会被屏蔽,不会被定向到钓鱼网站,如果网站没有使用加密的安全链接,可能会跳转到攻击者制作的钓鱼网站.可能直接被盗。
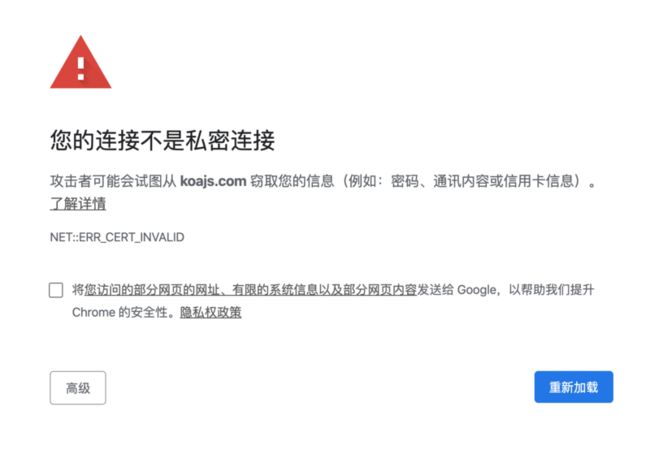
图片来自知乎网友
中间人攻击(简称MITM)是指攻击者接管通信两端的流量,攻击者可以拦截双方的通话并篡改内容。简而言之,所谓中间人攻击,就是拦截正常的网络通信数据已阻止此网站显示有安全证书错误的内容,在双方不知情的情况下进行数据篡改和嗅探。
后续信息,本文将继续跟进。
附部分节点测试情况
阿里云上海数据中心(BGP):
- curl -k -v https://z.github.io
- *Connected to z.github.io (185.199.108.153) port 443(#0)
- * SSL connection usingTLSv1.2/ ECDHE-ECDSA-AES128-GCM-SHA256
- * ALPN, server did not agree to a protocol
- *Server certificate:
- * subject: C=CN; ST=GD; L=SZ; O=COM; OU=NSP; CN=SERVER; emailAddress=346608453@qq.com* start date:Sep2609:33:132019 GMT
- * expire date:Sep2309:33:132029 GMT
- * issuer: C=CN; ST=GD; L=SZ; O=COM; OU=NSP; CN=CA; emailAddress=346608453@qq.com* SSL certificate verify result:selfsigned certificate in certificate chain (19), continuing anyway.
- > GET / HTTP/1.1
- >Host: z.github.io
- >User-Agent: curl/7.52.1
- >Accept:*/*
群英网络镇江数据中心(电信):
- curl -k -v https://z.github.io
- *Rebuilt URL to: https://z.github.io/
- *Trying185.199.108.153...
- * SSL connection usingTLSv1.2/ ECDHE-RSA-AES128-GCM-SHA256
- * ALPN, server accepted to use h2
- *Server certificate:
- * subject: C=US; ST=California; L=SanFrancisco; O=GitHub,Inc.; CN=www.github.com
- * start date:Jun2700:00:002018 GMT
- * expire date:Jun2012:00:002020 GMT
- * issuer: C=US; O=DigiCertInc; OU=www.digicert.com; CN=DigiCert SHA2 HighAssuranceServer CA
- * SSL certificate verify ok.
- *Using HTTP2, server supports multi-use
- *Connection state changed (HTTP/2 confirmed)
- *Copying HTTP/2 data in stream buffer to connection buffer after upgrade: len=0
- *UsingStream ID:1(easy handle 0x556d826f6ea0)
- > GET / HTTP/1.1
- >Host: z.github.io
- >User-Agent: curl/7.52.1
- >Accept:*/*
华为云香港数据中心(以下为正常连接的证书信息第44行):
- curl -k -v https://z.github.io
- *Rebuilt URL to: https://z.github.io/
- *Trying185.199.108.153...
- * SSL connection usingTLSv1.2/ ECDHE-RSA-AES128-GCM-SHA256
- * ALPN, server accepted to use h2
- *Server certificate:
- * subject: C=US; ST=California; L=SanFrancisco; O=GitHub,Inc.; CN=www.github.com
- * start date:Jun2700:00:002018 GMT
- * expire date:Jun2012:00:002020 GMT
- * issuer: C=US; O=DigiCertInc; OU=www.digicert.com; CN=DigiCert SHA2 HighAssuranceServer CA
- * SSL certificate verify ok.
- *Using HTTP2, server supports multi-use
- *Connection state changed (HTTP/2 confirmed)
- *Copying HTTP/2 data in stream buffer to connection buffer after upgrade: len=0
- *UsingStream ID:1(easy handle 0x556d826f6ea0)
- > GET / HTTP/1.1
- >Host: z.github.io
- >User-Agent: curl/7.52.1
- >Accept:*/*










